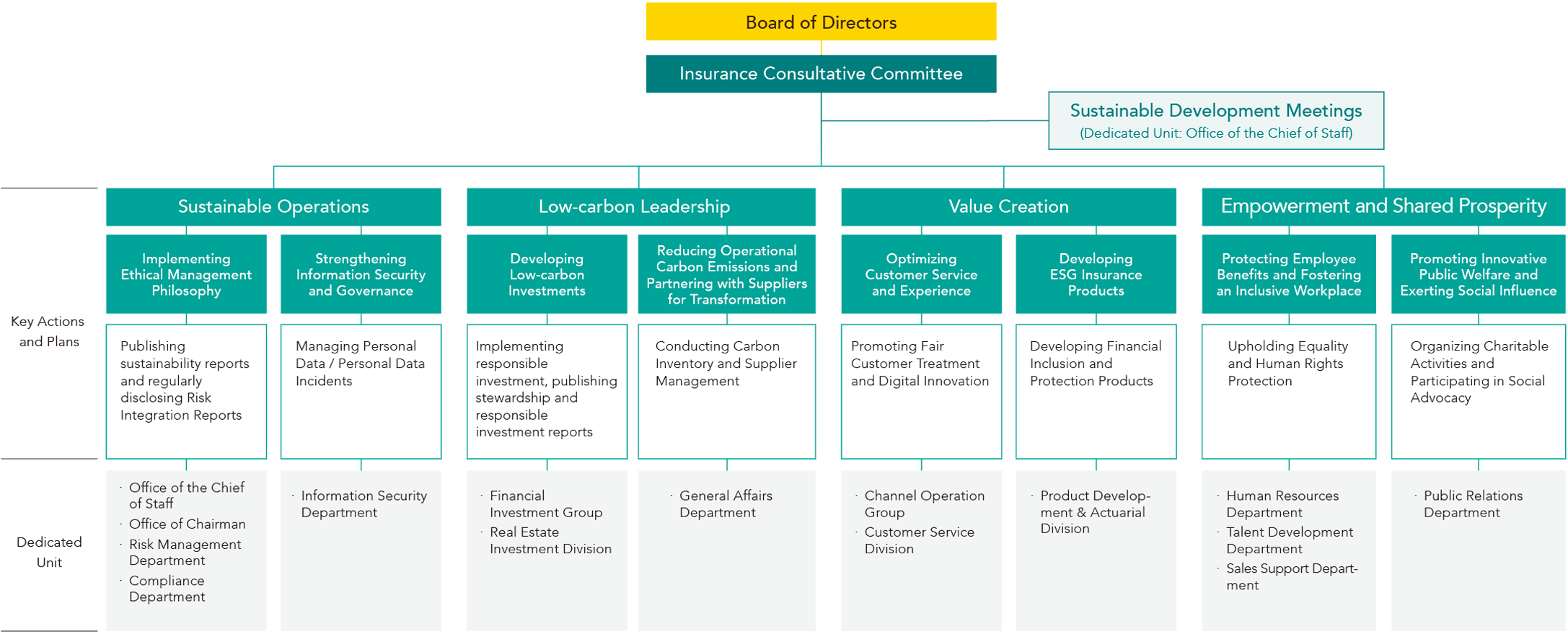
Taiwan Life's Board of Directors serves as the highest governing body for sustainability governance, with the President appointed as the management officer responsible for ESG performance. A dedicated ESG unit has also been established to coordinate relevant issues. In 2023, the Insurance Consultative Committee initiated quarterly Sustainable Development Meetings composed of senior executives. The meetings monitor the implementation of ESG initiatives and report on new sustainability trends. In 2024, a total of 12 Sustainable Development Meetings were held.
● Taiwan Life Sustainability Governance Structure
As of February 2025